And, if you are using WordPress, then in another report by SUCURI shows, 49% of scanned websites were outdated.
As a web application owner, how do you ensure your site is protected from online threats? Doesn’t leak sensitive information? If you are using a cloud-based security solution, then most likely, regular vulnerability scanning is part of the plan. However, if not, then you got to perform a routine scan and take necessary action to mitigate the risks. There are two types of scanner. Commercial – give you an option to automate the scanning for continuous security, reporting, alerting, detailed mitigation instructions, etc. Some of the known names in the industry are:
Acunetix Detectify Qualys
Open Source/Free – you can download and perform a security scan on-demand. Not all of them will be able to cover a broad range of vulnerabilities like a commercial one. Let’s check out the following open source web vulnerability scanner.
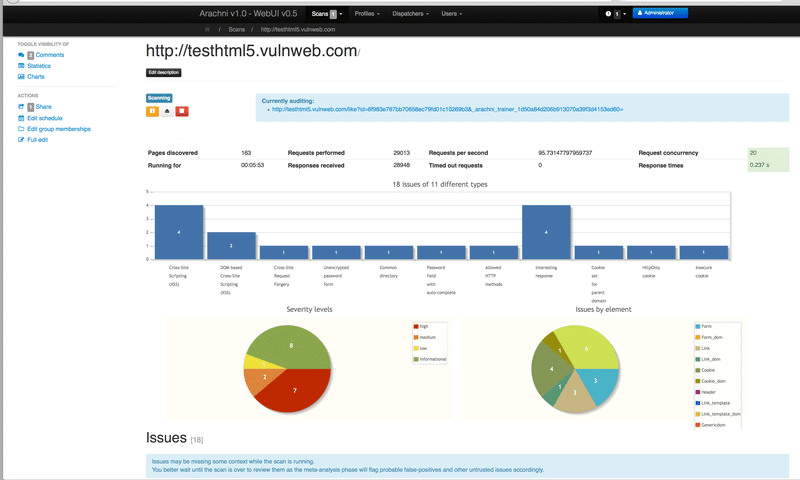
Arachni
Arachni, a high-performance security scanner built on Ruby framework for modern web applications. It is available in a portable binary for Mac, Windows & Linux.
Not just basic static or CMS website, but Arachni is capable of doing following platform fingerprints. It performs active & passive checks, both.
Windows, Solaris, Linux, BSD, Unix Nginx, Apache, Tomcat, IIS, Jetty Java, Ruby, Python, ASP, PHP Django, Rails, CherryPy, CakePHP, ASP.NET MVC, Symfony
Some of the vulnerabilities detection are:
NoSQL/Blind/SQL/Code/LDAP/Command/XPath injection Cross-site request forgery Path traversal Local/Remote File inclusions Response splitting Cross-site scripting Unvalidated DOM redirects Source code disclosure
You have an option to take an audit report in HTML, XML, Text, JSON, YAML, etc. Arachni lets you extend the scan to the next level by leveraging plugins. Check out the complete Arachni features and download to experience it.
XssPy
A python-based XSS (cross-site scripting) vulnerability scanner is used by many organizations, including Microsoft, Stanford, Motorola, Informatica, etc. XssPy by Faizan Ahmad is a smart tool. It does one thing ut pretty well. Instead of just checking the home page or given page, it checks the entire link on the websites. XssPy also checks the subdomain, so nothing is left out.
w3af
w3af, an open-source project started back in late 2006, is powered by Python and available on Linux and Windows OS. w3af is capable of detecting more than 200 vulnerabilities, including OWASP top 10.
w3af let you inject payloads to headers, URL, cookies, query-string, post-data, etc. to exploit the web application for auditing. It supports various logging method for reporting. Ex: Ex:
CSV HTML Console Text XML Email
It’s built on a plugin architecture, and you can check out all the plugins available here.
Nikto
An open-source project sponsored by Netsparker aims to find web server misconfiguration, plugins, and web vulnerabilities. Nikto perform a comprehensive test against over 6500 risk items. It supports HTTP proxy, SSL, with or NTLM authentication, etc. and can define maximum execution time per target scan. Nikto is also available in Kali Linux.
It looks promising for the intranet solution to find web servers security risks.
Wfuzz
Wfuzz (The Web Fuzzer) is an application assessment tool for penetration testing. You can fuzz the data in the HTTP request for any field to exploit the web application and audit the web applications. Wfuzz required having Python installed on the computer where you want to run the scan. It got excellent documentation for you to get it started.
OWASP ZAP
ZAP (Zet Attack Proxy) is one of the famous penetration testing tools which is actively updated by hundreds of volunteer worldwide. It’s a cross-platform Java-based tool that can run even on Raspberry Pi. ZIP sits between a browser and web application to intercept and inspect messages
Some of the following are worth mentioning ZAP’s functionality.
Fuzzer Automated & passive scanner Supports multiple scripting languages Forced browsing
I would highly recommend to check out OWASP ZAP tutorial videos to get it started.
Wapiti
Wapiti scans the web pages of a given target and looks for scripts and forms to inject the data to see if that is vulnerable. It is not a source code security checks; instead, it performs black-box scans.
It supports GET and POST HTTP method, HTTP and HTTPS proxies, several authentications, etc.
Vega
Vega is developed by Subgraph, a multi-platform supported tool written in Java to find XSS, SQLi, RFI, and many other vulnerabilities. Vega got a nice GUI and capable of performing an automated scan by logging into an application with a given credential.
If you are a developer, you can leverage vega API to create new attack modules.
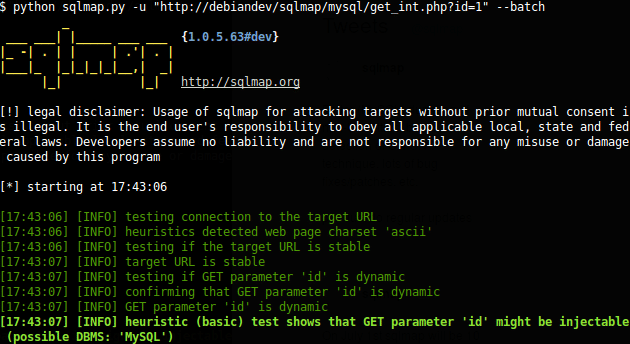
SQLmap
As you can guess by the name, with the help of the sqlmap, you can perform penetration testing on a database to find flaws.
It works with Python 2.6 or 2.7 on any OS. If you are looking to find SQL injection and exploit the database, then sqlmap would be helpful.
Grabber
It’s a small tool based on Python and does a few things quite well. Some of the Grabber’s features are:
JavaScript source code analyzer Cross-site scripting, SQL injection, Blind SQL injection PHP application testing using PHP-SAT
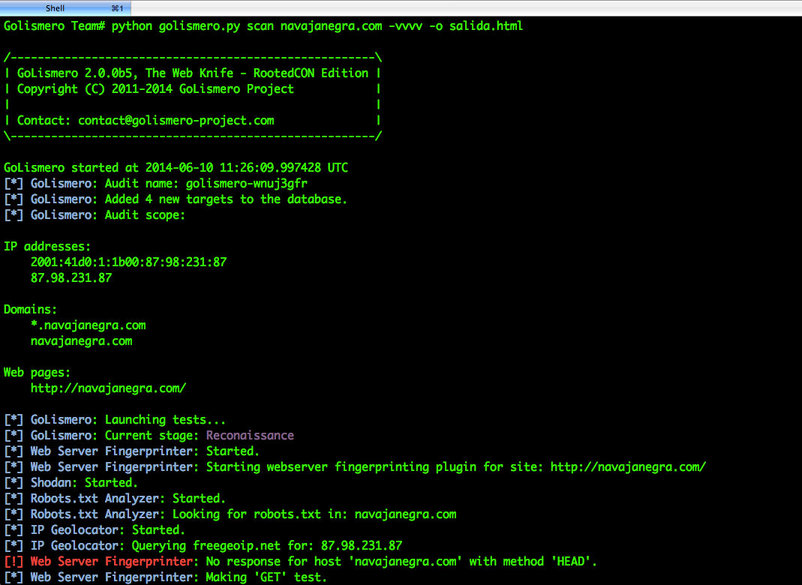
Golismero
A framework to manage and run some of the popular security tools like Wfuzz, DNS recon, sqlmap, OpenVas, robot analyzer, etc.).
Golismero is smart; it can consolidated test feedback from other tools and merge to show a single result.
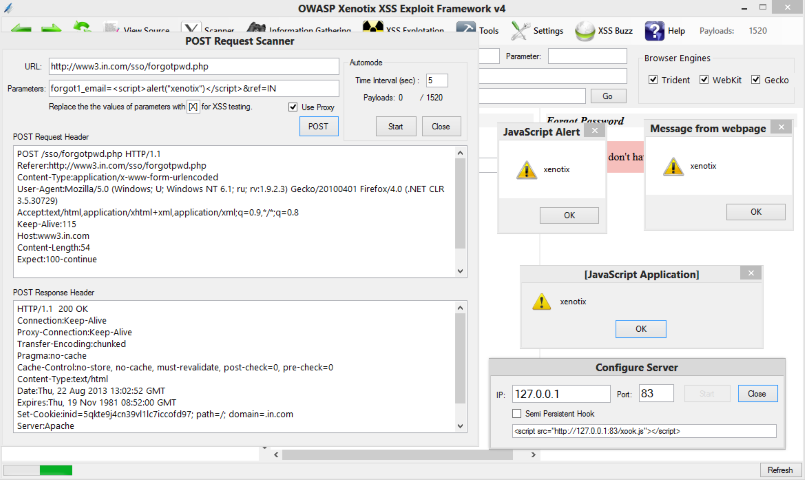
OWASP Xenotix XSS
Xenotix XSS by OWASP is an advanced framework to find and exploit cross-site scripting. It got inbuilt three intelligent fuzzers for a fast scan and improved results.
It got hundreds of features, and you can check out all listed here.
Conclusion
Web security is critical to any online business, and I hope above listed free/open-source vulnerability scanner helps you to find risk so you can mitigate before someone take advantage of it. If you are interested in learning about penetration testing then check out this online course.

![]()